Awe-Inspiring Examples Of Tips About How To Avoid The Wpa Wireless Security Standard Attack
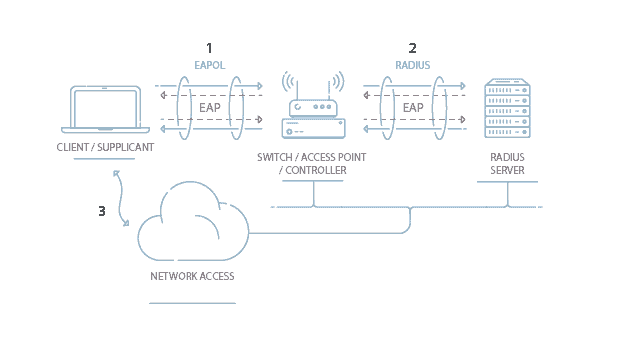
Wpa2 operates on two modes — personal (pre.
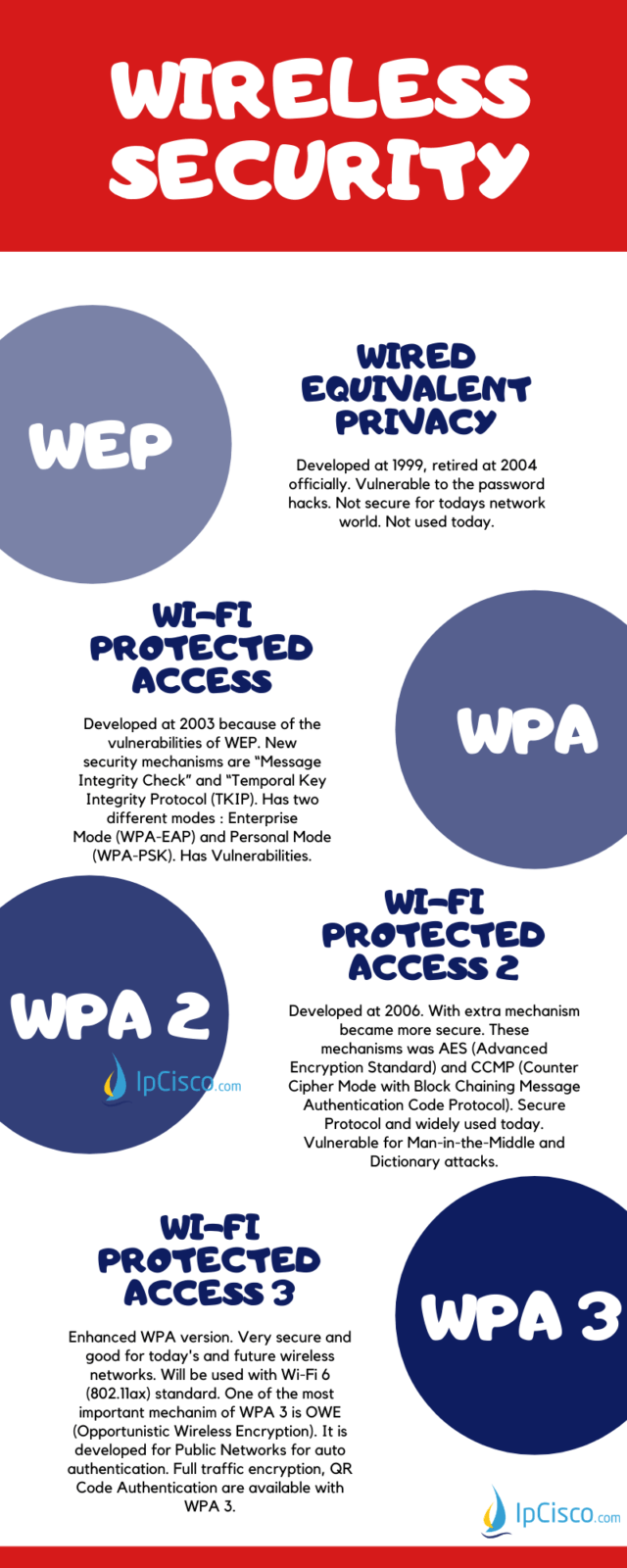
How to avoid the wpa wireless security standard attack. Avoid actual words and distribute the characters randomly. When choosing from among wep, wpa,. This article also takes a deep dive into the history and technical details of wep, wpa, wpa2 and wpa3.
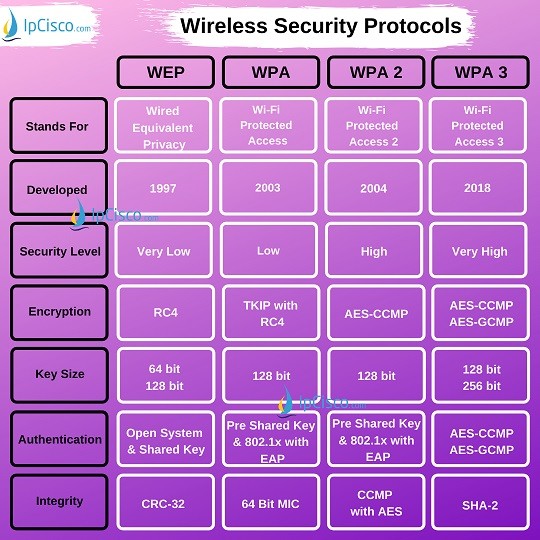
In that case, the next best option is wpa2, which. As more and more network vulnerabilities are being discovered, we should always plan our security measures and get one step ahead of the attackers. Wireless protected access (wpa) wireless protected access 2 (wpa2) washington university in st.
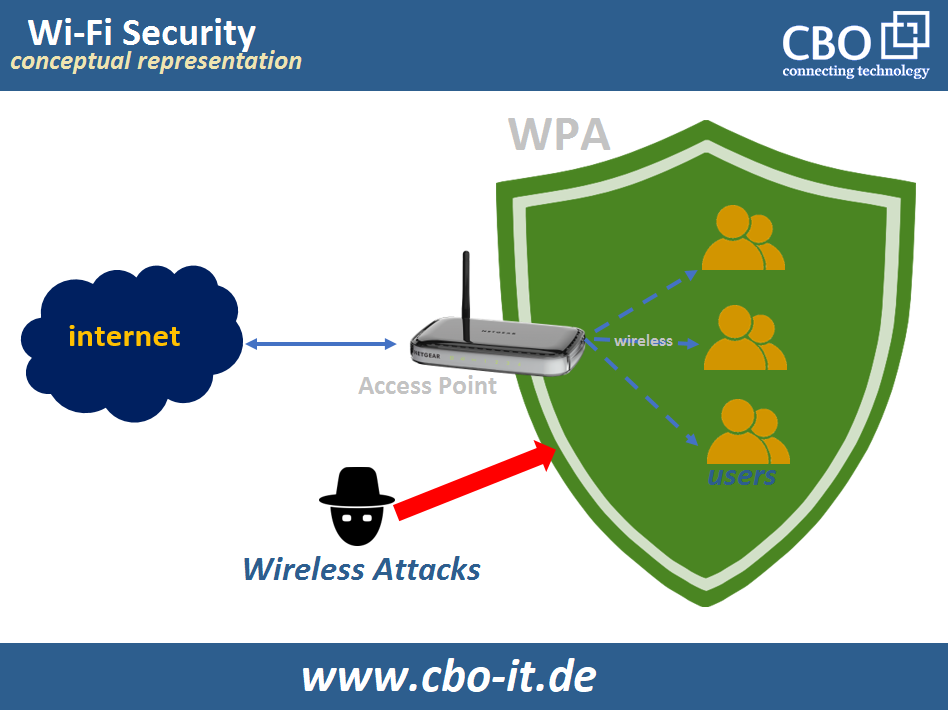
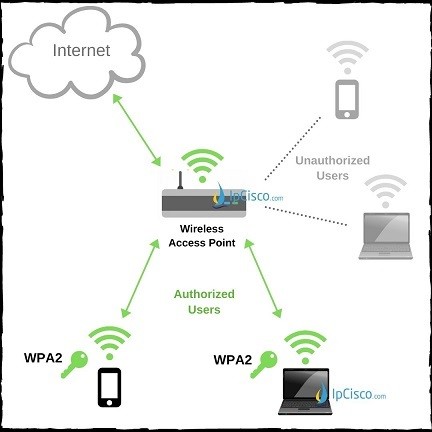
A properly implemented password with enough entropy can withstand even a very. As you go down the list, you are getting less security for your network. Wireless security is concise on protecting the resources connected to the wireless network from unauthorized access.
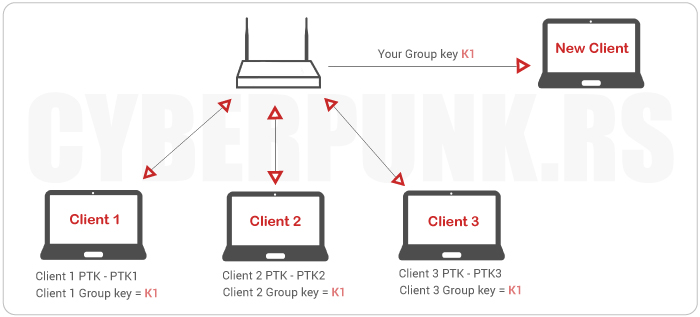
All access points and subscribers need to use wpa wpa+wep ⇒wep separate keys for authentication, encryption, and integrity 48b tkip sequence counter (tsc) is used to generate. We can avoid unsecured wireless. You can also keep the wlan password on paper in a safe place, just don’t write in on your computer.
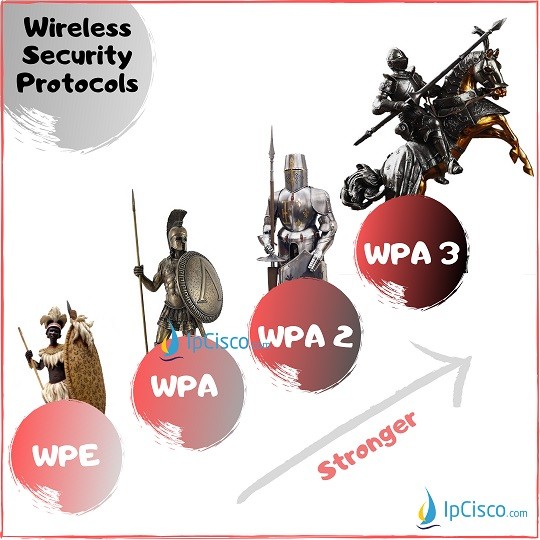
Wpa2, launched in 2004, is the upgraded version of wpa and is based on the robust security network (rsn) mechanism. Some wireless aps do not support wpa3, however.